It will be a few more years before quantum computers arrive, but the threat they represent is already here.
The urgency surrounding post-quantum security stems from the fact that our sensitive data remains at risk until we adapt to quantum-resistant cryptographic algorithms. Medical records, financial transactions, intellectual property, online communications, and other critical aspects of our digital lives rely on encryption to maintain privacy and security. Without adequate post-quantum security measures in place, these pillars of our interconnected world could crumble, leaving individuals and organisations vulnerable to attacks.
What is quantum computing?
Quantum computing technology is based on quantum physics principles and the concepts of superposition and entanglement.
Traditional computers use bits, which can have a value of either a 0 or a 1, and process information by manipulating these bits using logic gates (AND, OR, NOT).
Quantum computers use quantum bits, called qubits. Unlike bits, qubits can represent both 0 and 1 simultaneously. This is due to a property called superposition in quantum mechanics. When qubits are entangled, a change in the state of one qubit is instantly reflected in the state of the other qubit(s). Quantum computers can handle operations at speeds that are orders of magnitude faster than traditional computers or supercomputers. According to a 2019 research, “With 20 qubits, the number of superimposed states already exceeds one million. And 300 qubits can store more numbers simultaneously than there are particles in the universe.”.
In 2022, IBM unveiled Osprey, which boasts the largest qubit count of any IBM quantum processor, more than tripling the 127 qubits on the IBM Eagle processor launched in 2021. The new processor can handle complex quantum computations beyond the capability of any classical computer. The number of classical bits required to represent a state on the IBM Osprey processor exceeds the total number of atoms in the known universe.
Quantum computing has the potential to advance lots of industries, but there are many challenges to overcome before it becomes generally available (hardware, scalable architecture, talent, etc.).
What is the biggest security threat in the context of quantum computing?
Malicious third parties can collect data today, data that will maintain its value for a long time, and then wait until they can decrypt it. This type of attack is referred to as “harvest now, decrypt later“. When quantum computing becomes available, breaking public-key cryptography will only take seconds.
Public key cryptography is widely used in our daily lives, and some notable examples include:
- TLS, which secures the key exchange when connecting to a website thus ensuring that future communications are encrypted;
- PKI, which utilizes a private and public key for authentication and encryption;
- messaging applications that require a pair of private and public keys;
- email encryption;
- cryptocurrencies, which also rely on a public and a private key.
The risk of quantum computing cannot be ignored, and without encryption, it may be necessary to disengage from ICT infrastructure, which is impractical for most applications, such as financial transactions, online communications, or e-health.
What is CryptoNext and how do they address the post-quantum security issues?
To protect against this “harvest now, decrypt later” tactic, the French startup CryptoNext has developed a hybrid post-quantum cryptographic library that allows users to protect their data now against various types of threats. To achieve this, the CryptoNext solution offers end-to-end post-quantum remediation tools and solutions for IT/OT infrastructures and applications, combining classical and post-quantum encryption algorithms, similar to those predicted by the National Institute of Standards and Technology (NIST) for future cryptographic standard.
With CryptoNext’s Quantum Safe Software Suite, seamless integration of post-quantum cryptography is made possible for embedded systems, as well as for commonly used communication and authentication infrastructures, systems, and applications.
The multi-layered framework includes a crypto library, protocols, objects, development tools, and application plugins.
- C-QSL (Library)
The CryptoNext Quantum Safe Library (C-QSL) is a high-performance library layer that includes the core technology used in all of CryptoNext’s products. This library is designed to be flexible and to support various post-quantum cryptography algorithms, including the NIST selection and EU National Agencies’ recommendations. It is developed in both C and ASM to optimize performance across different operating systems and processing units. Additionally, it has APIs to upgrade IT equipment, applications, and security infrastructures to pure or hybrid quantum-safe security. C-QSL supports key exchange mechanisms such as Kyber and FrodoKEM, digital signature algorithms such as Dilithium, Falcon, Sphincs+, and XMSS, and has language wrappers for Go, Rust, Python, and Java. The library also includes a deterministic random bit generator that produces unpredictable bit sequences.
- C-QSC (Services)
The CryptoNext Quantum Safe Crypto Services (C-QSC) is a layer that provides pure post-quantum (PQ) or hybrid PQ communication protocols, cryptographic objects, and programming interfaces. These protocols are critical for crypto-agility, hybridization, and interoperability standards and are based on existing or in-progress RFCs from organizations such as IETF. This layer relies on the new PQ algorithms from the Library layer and is implemented in the upper Tools layer. It includes upgraded PKCS#11 (Cryptoki C-level) with pure/hybrid PQ for HSM functions call and communication protocols such as PQ IKE for IPSec, PQ TLS, PQ S/MIME (CMS-SIG; CMS-KEM), and PQ X3DH Signal Messaging Protocol.
- C-QST (Tools)
The CryptoNext Quantum Safe Integration Tools (C-QST) serve as a product layer specifically designed for Pure PQ and Hybrid PQ implementations in common development tools. These plug-and-play products enable developers to migrate applications to achieve quantum resilience with minimal modifications and without requiring specialized post-quantum cryptography (PQC) skills. C-QST tools make use of the hybrid PQ protocols and cryptographic objects available in the C-QSC layer while relying on the core CryptoNext Quantum Safe Library (C-QSL).
- C-QSA (Applications)
The CryptoNext Quantum Safe Application Plugins (C-QSA) products provide a range of PQ implementations for secured communications, systems, networks, and security infrastructures. C-QSA has plugins for popular VPN, HSM, PKI, web servers, and blockchain platforms. The PQ Secured Messaging feature is available for both Android and iOS. Network infrastructure plugins include StrongSwan PQ VPN IPSec (Server/Client), PQ OpenVPN, and PQ OpenSSH (Network Admin). System infrastructure plugins are available for Apache Tomcat and Node.js. Security infrastructure includes PQ PKI based on the EJBCA Community, HSM Luna7 Network Appliance-based PQ FM, HSM Luna7 PCI Board-based PQ FM, and Corda-based PQ Blockchain.
Steps toward implementing post-quantum cryptography
Migration to post-quantum cryptography is mandatory. To achieve operational efficiency, simplicity, and long-term sustainability, organizations will need to implement an intelligent, fully managed post-quantum assessment and extensive remediation across their entire infrastructure.
The steps outlined by CryptoNext are:
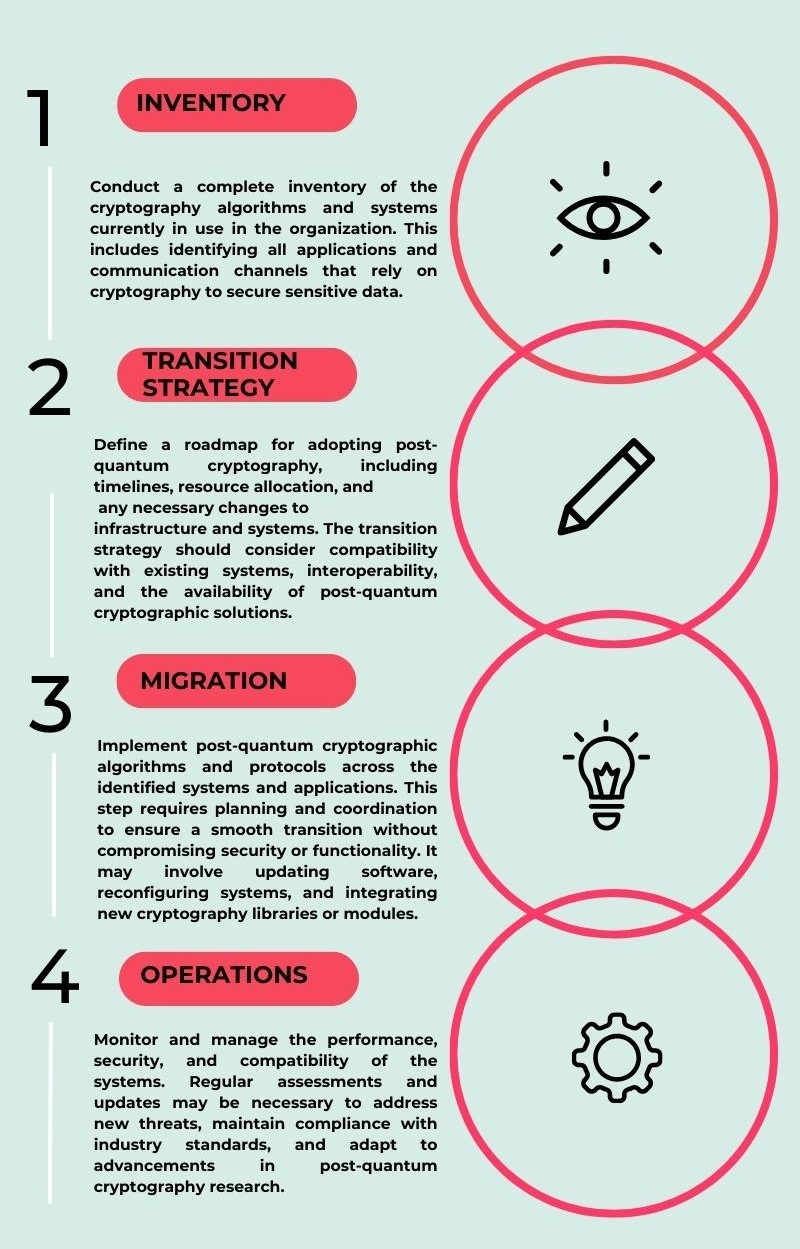
(Steps toward implementing post-quantum cryptography. Source: CryptoNext)
In conclusion
CryptoNext’s efforts in post-quantum security highlight the critical importance of transitioning to quantum-resistant cryptography. By understanding the risks of quantum computing and embracing innovative solutions, we can protect our sensitive data and build a resilient digital future.
Start preparing today for the threats of tomorrow
Don’t wait until it’s too late to safeguard your valuable data. While banks and defense companies are traditionally the first to implement changes, be proactive and act now to stay ahead of the game. Protect your organization against post-quantum security threats and maintain a competitive edge. Consult with our experts today and secure your future.
This article and infographic are part of a larger series centred around the technologies and themes found within the 2023 edition of the TechRadar by Devoteam report. To learn more about CryptoNext and other technologies you need to know about, please download the TechRadar by Devoteam .

